Africa DFIR CTF Week 1
Category: Digital Forensics
Challenge : Week 1
Deleted:
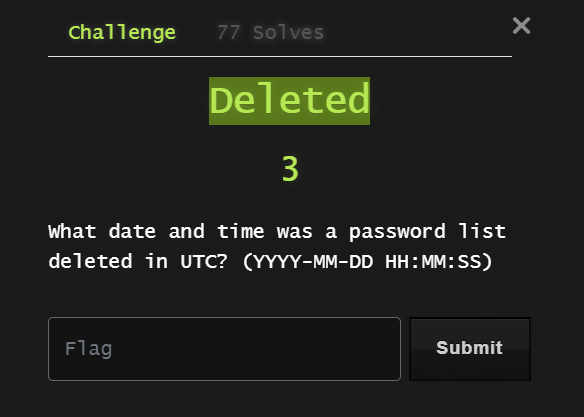
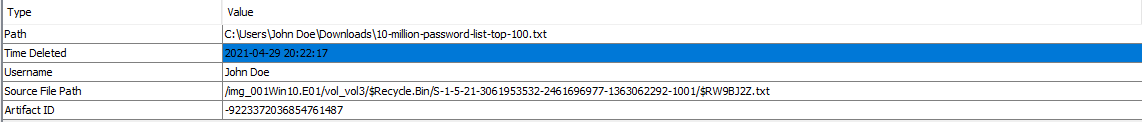
As we see from the name of the challenge “Deleted”. so what we will search for will be in Recycle Bin (artifact). in my case i will use autopsy, you can use any other tool. if we go to Recycle bin we will find one txt file that deleted and here’s the flag :
Server Connection:
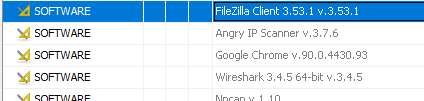
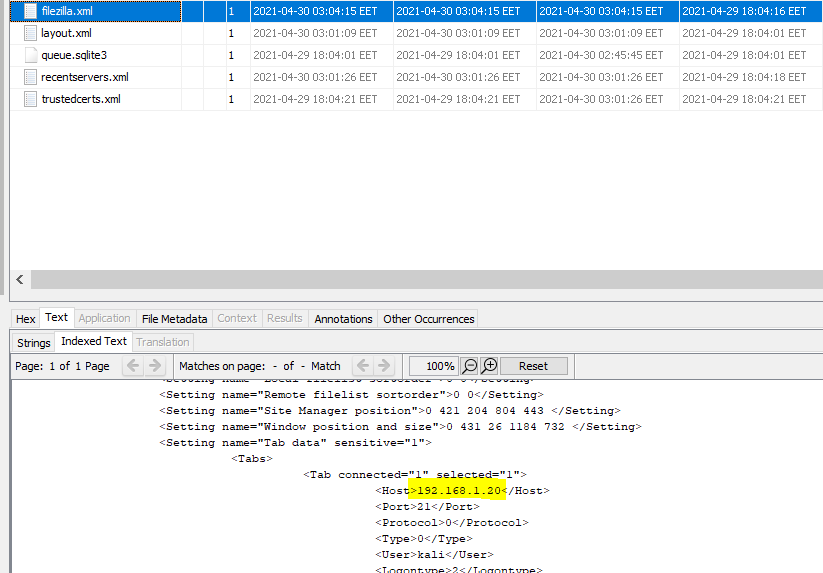
here we talk about IPv4 of FTP server so first let’s see what app the user use. so let’s go to installed Programs in autopsy.
as we see here he used FileZilla Client 3.53.1 v.3.53.1. In the case of FileZilla our source of evidence is the XML configuration files that FileZilla leaves behind in the %user%\appdata\roaming\filezilla directory(FileZilla Artifacts).as we see here :
Suspect Disk Hash:
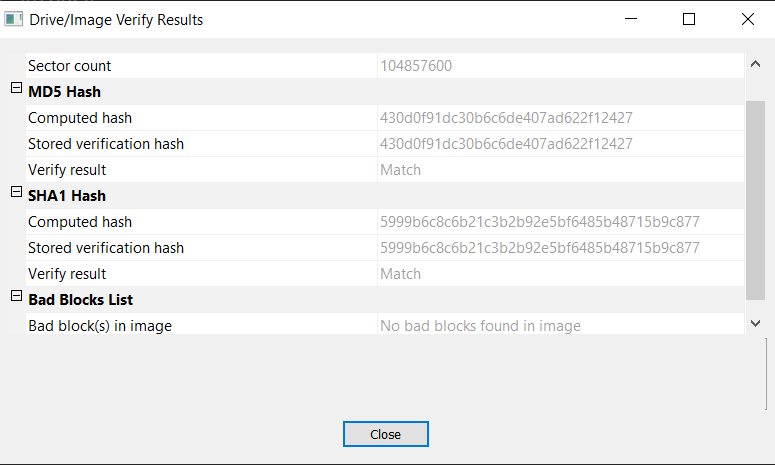
here we will use FTK Imager to import the disk image 001Win10.E01 and calculate the hash of the disk , then we will find the md5 hash.
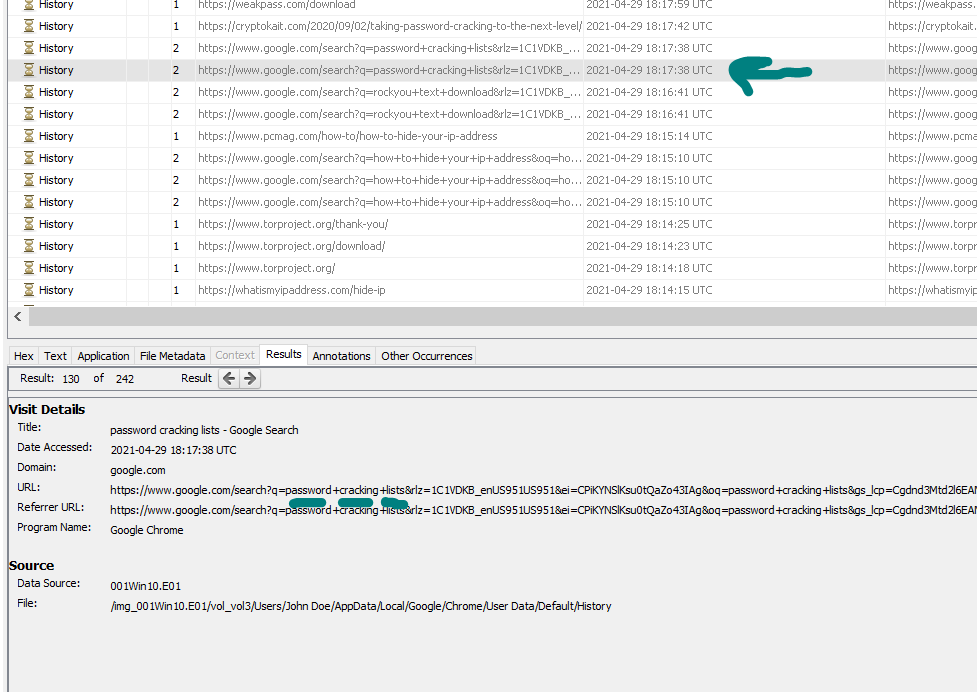
Web Search:
in this challenge we need first to convert the time to UTC to be easy for us :
then we will go to web history and we will find the flag :
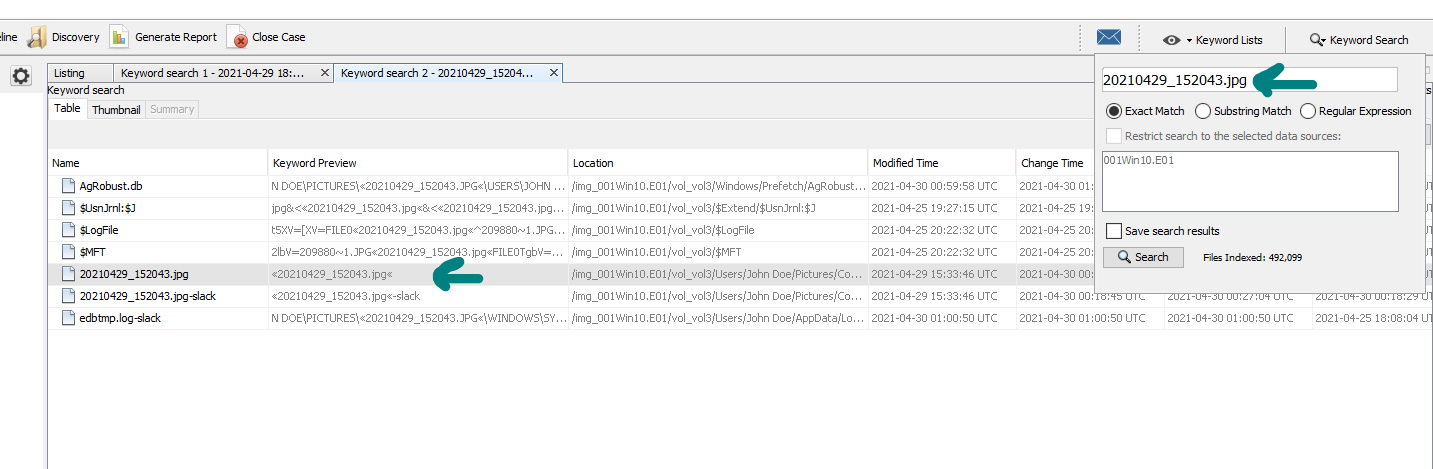
Possible Location:
here we can use two ways one to go to exif metadata (Autopsy Ingest Module) to find the photo or to use keyword search :
then we can extract the photo from autopsy and use exiftool or any online tool to get the location of the photo :
Tor Browser:
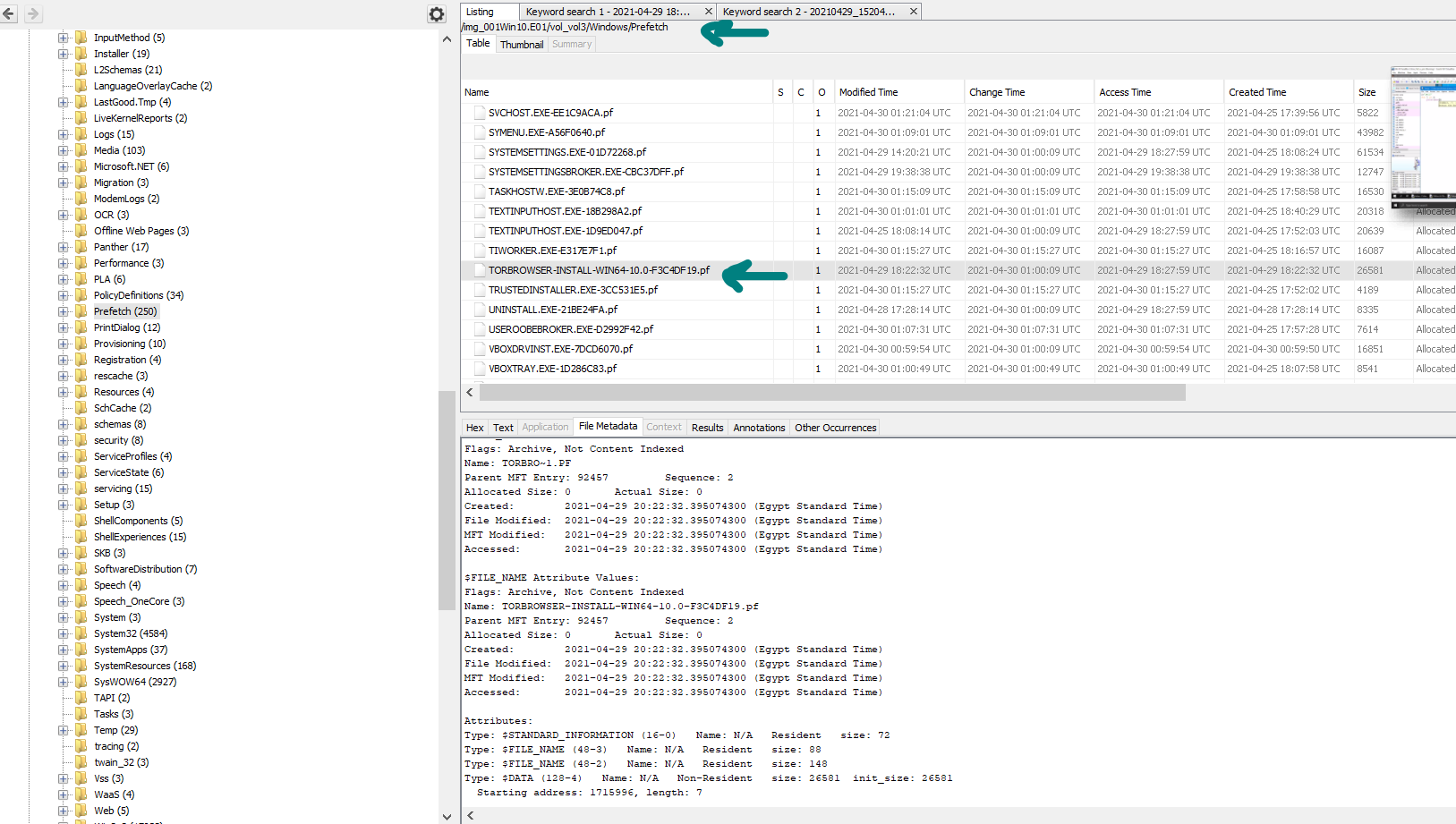
Here we will look at tor prefetch artifact under \Windows\Prefetch :
here we can’t see run count or last executed that means that the suspect only installed tor but didn’t use it :( .
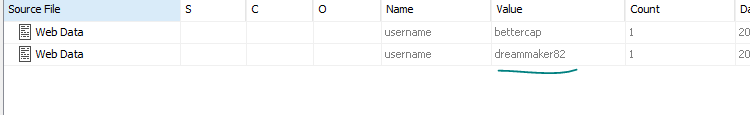
User Email:
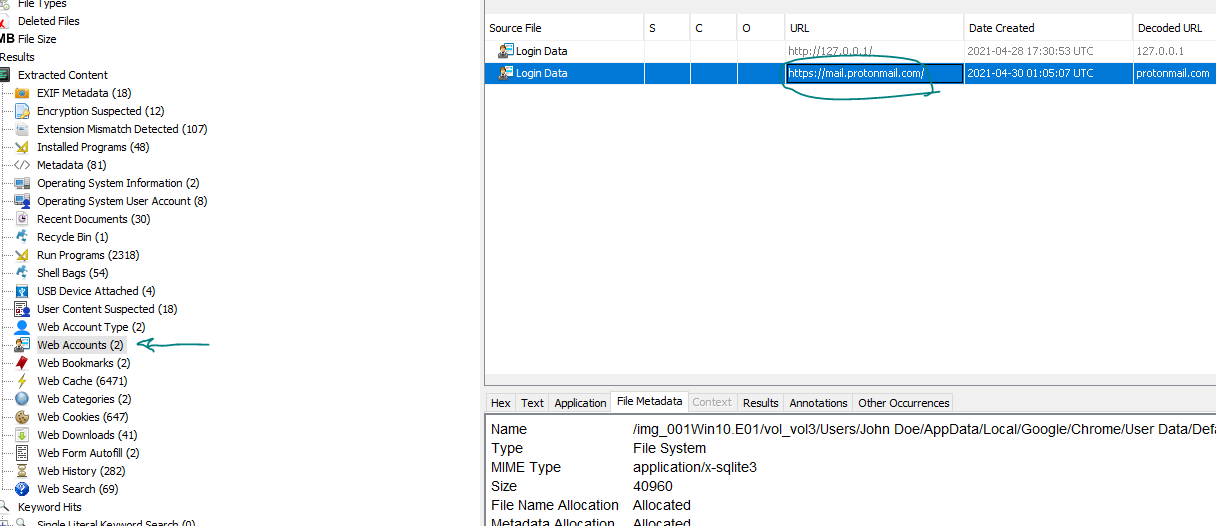
here we can go to Web Accounts in autopsy and we will find that the user uses protonmail:
so we can next go to Web From Autofill and we will see the username:
by that we got the User Email :).
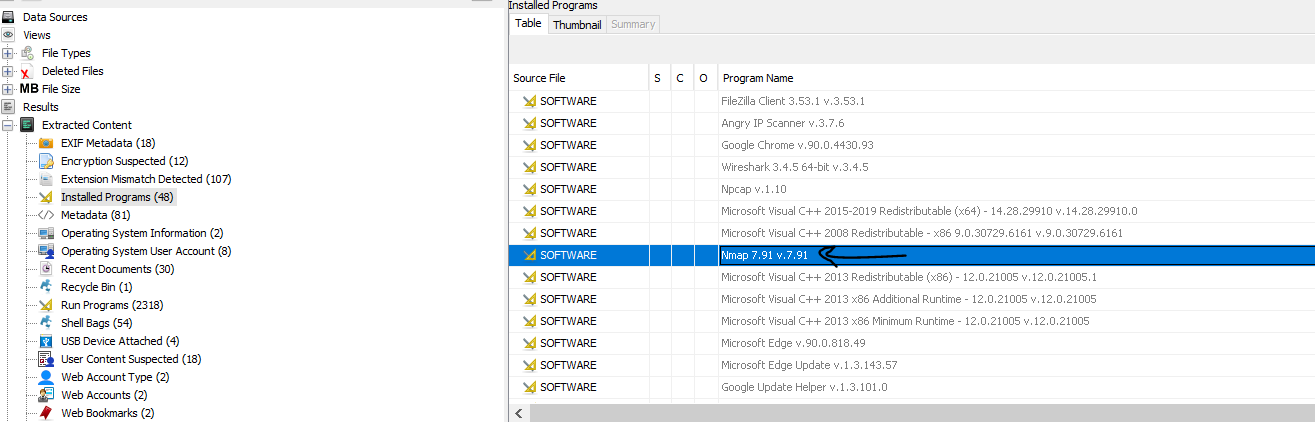
Web Scanning:
when we see port scan so we can guess that he use like nmap or other tool to make port scan. so let’s see. we can check installed programs in autopsy to see what apps did the suspect installed to make port scan :
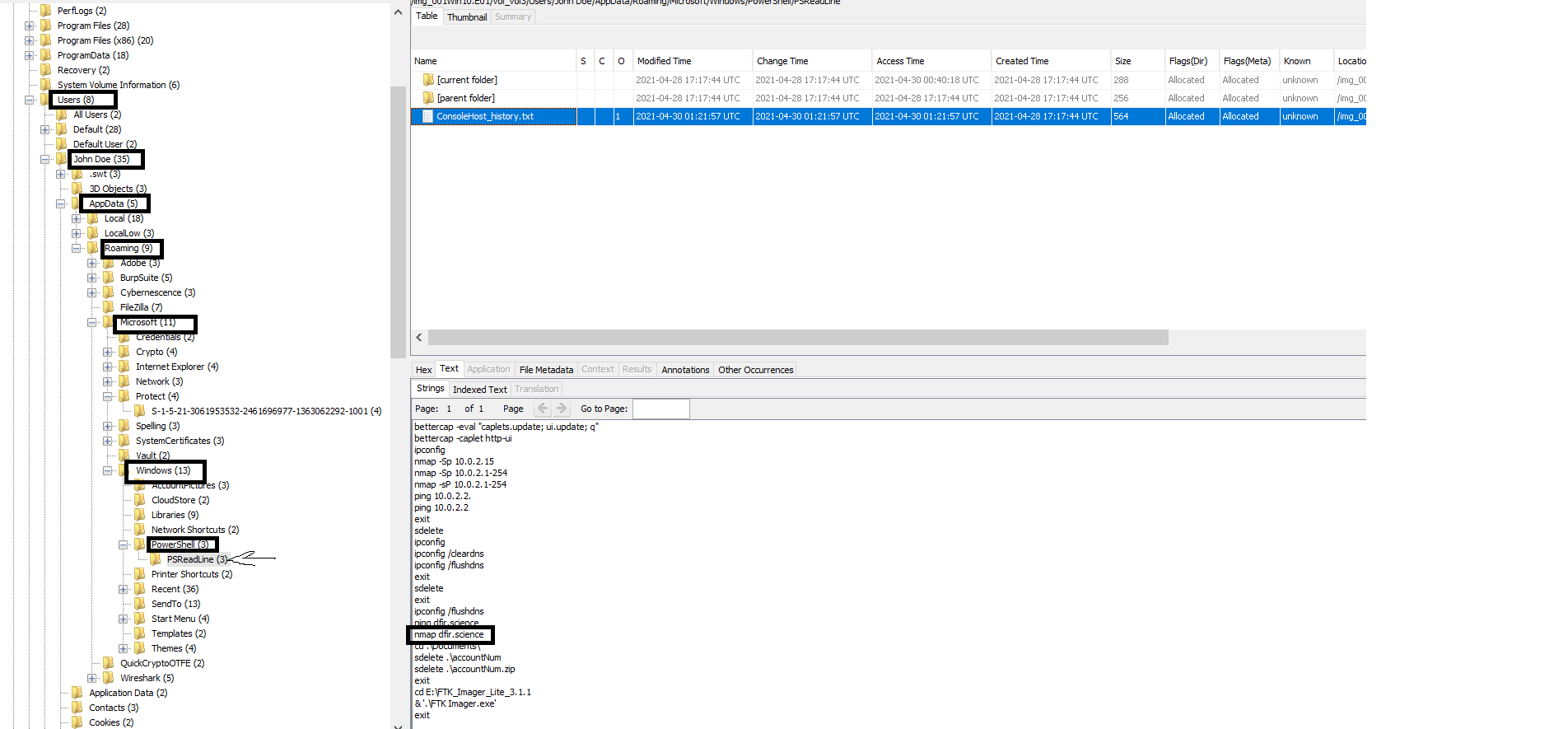
like we guessed that the user installed and used nmap to make port scan.so to get the command that the user entered to make port scan we can check Command History in PowerShell. By default, the PowerShell in Windows 10 saves the last 4096 commands that are stored in a plain text file located in the profile of each user %userprofile%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt, and here we can get the flag.
Copy Location:
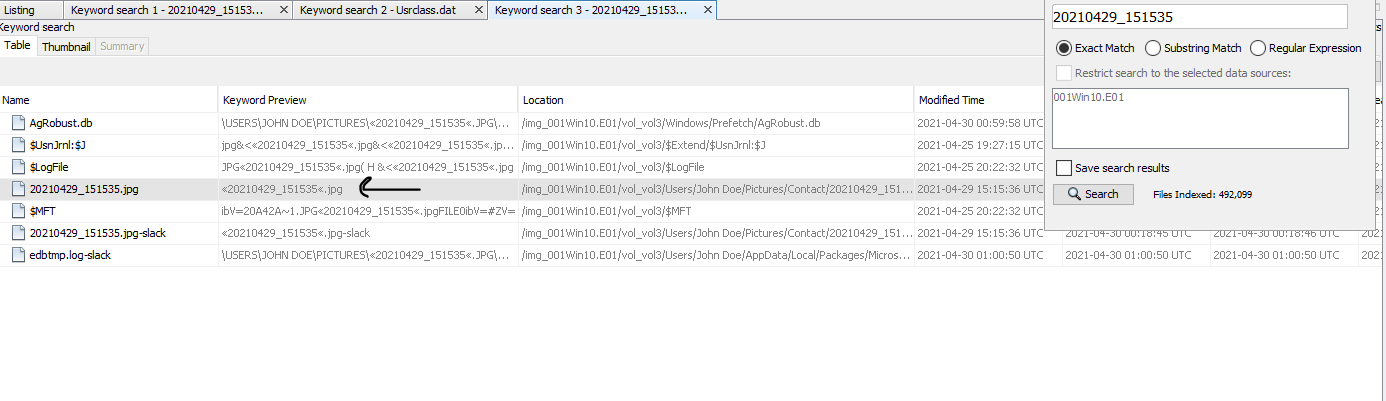
first i made a keyword search to find the photo.
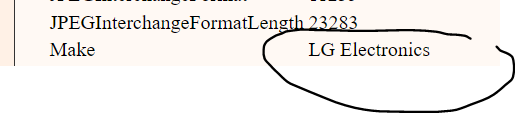
then we will use any online tool to extract metadata or we can use exiftool.
After we see LG Electronics so what come to my mind are ShellBags are a popular artifact in Windows forensics often used to identify the existence of directories on local, network, and removable storage devices. ShellBags are stored as a highly nested and hierarchal set of subkeys in the UsrClass.They are are a set of subkeys in the UsrClass.dat registry hive of Windows 10 systems. The shell bags are stored in both NTUSER.DAT and USRCLASS.DAT:
NTUSER.DAT: HKCU\Software\Microsoft\Windows\Shell
USRCLASS.DAT: HKCU\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell
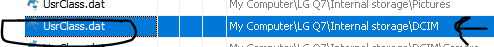
in Autopsy we can go to shellbags and get the flag DCIM :
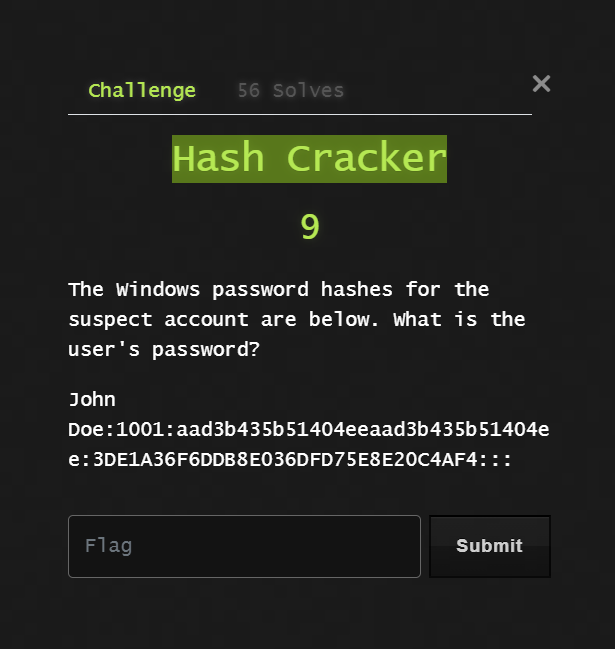
Hash Cracker:
by using google we can identify the hash type which is NTLM Hash you can read about it Here.
we can use two ways to bruteforce the first one with hashcat , the second one with any online tool the easy way ^^.
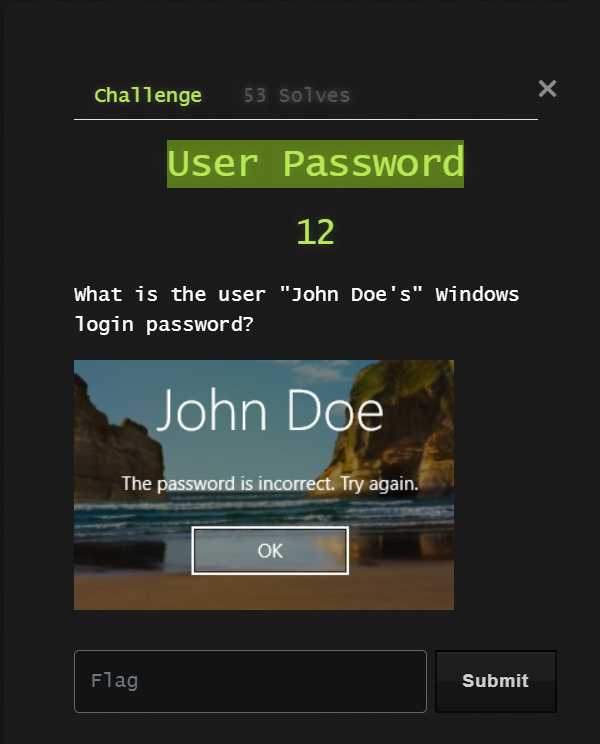
User Password:
what come to my mind when i saw Windows login password ?
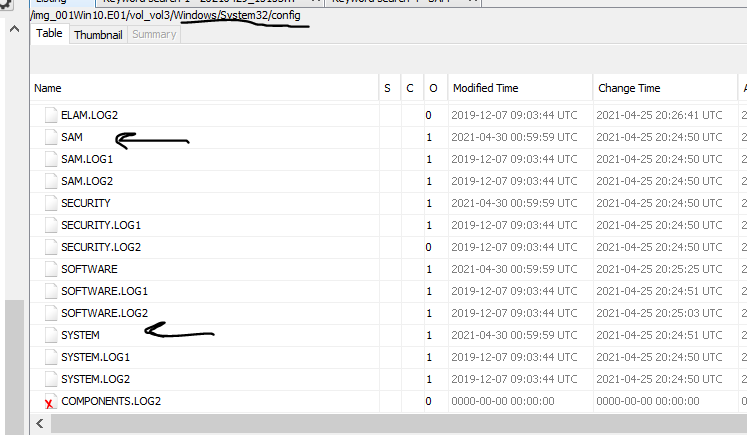
that we need to go to Registry artifacts in a Windows system because it functions as a database that stores various system configurations every second HKEY_CURRENT_CONFIG: Stores information from the hardware profile that is being used on the current system.
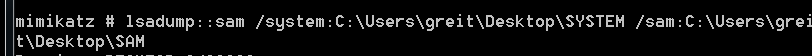
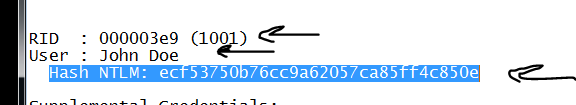
what we need to extract is HKEY_LOCAL_MACHINE \ SAM and HKEY_LOCAL_MACHINE \ System .After Extract them i will use mimikatz to get the user hash from extracted Registry Hives.
the user NTLM hash :
then we will crack the hash i used the same online tool to crack it we can also use hashcat or john the ripper.then we will get the flag :).
useful resource : windows-forensic-analysis
i hope you enjoy this :) , if you have any question contact me.